
INTELIGENCIA POLÍTICA & SOCIAL LISTENING
Soluciones de tecnopolítica
Social Listening como eje transversal en el tratamiento y análisis de datos
Extraemos datos de:












Nuestras soluciones
Social Listening como eje transversal en el tratamiento y análisis de datos
Political Insights
dentificación permanente de tendencias y estados de opinión
Perfil y percepción del electorado
CONOCIMIENTO Y ANÁLISIS DEL VOTANTE IDEAL
Gestión de comunicación institucional y política
ANÁLISIS DE LA EFICIENCIA DE LA COMUNICACIÓN EN LOS CANALES DIGITALES
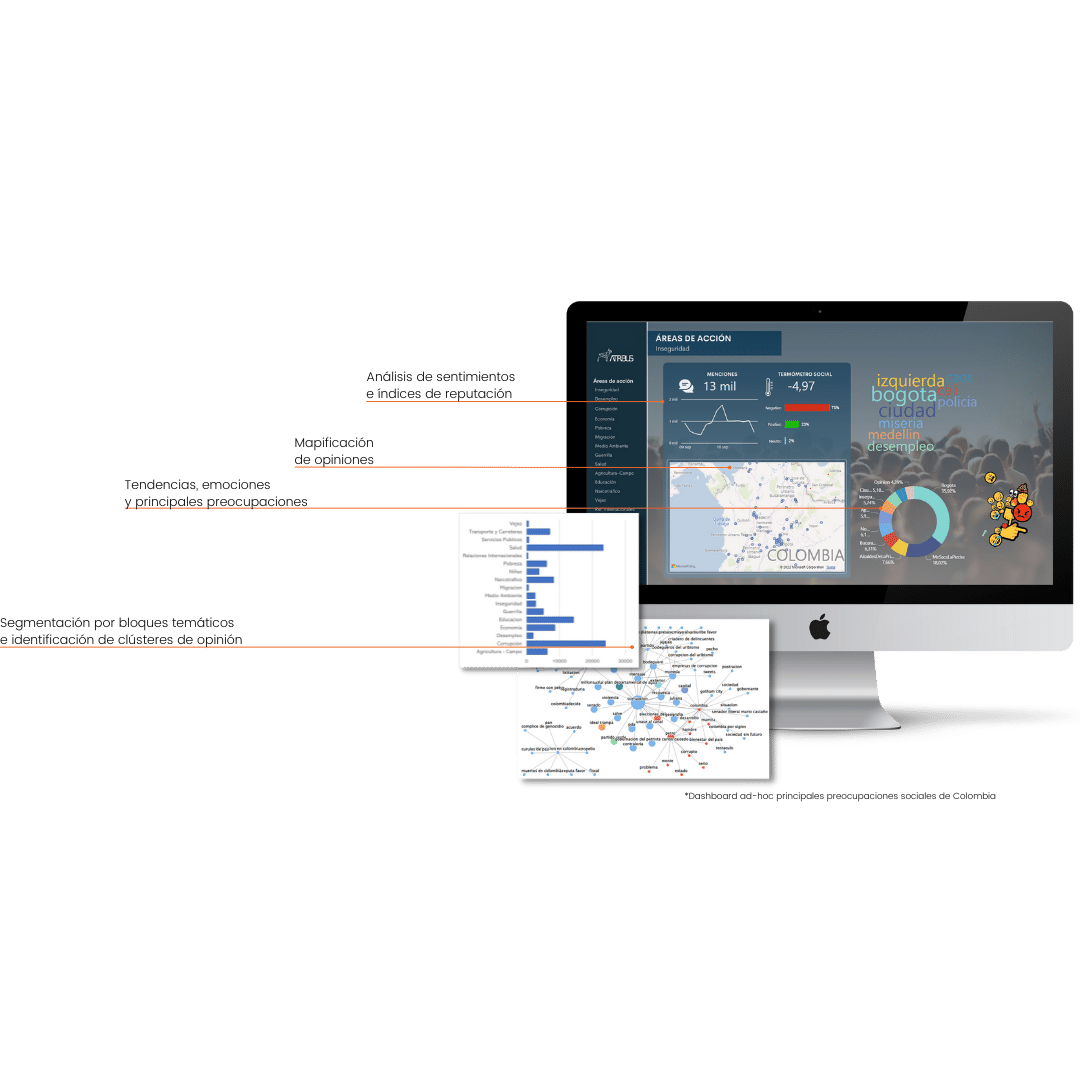
Análisis de reputación
REACCIONES Y EMOCIONES QUE DESPIERTA CADA CANDIDATURA
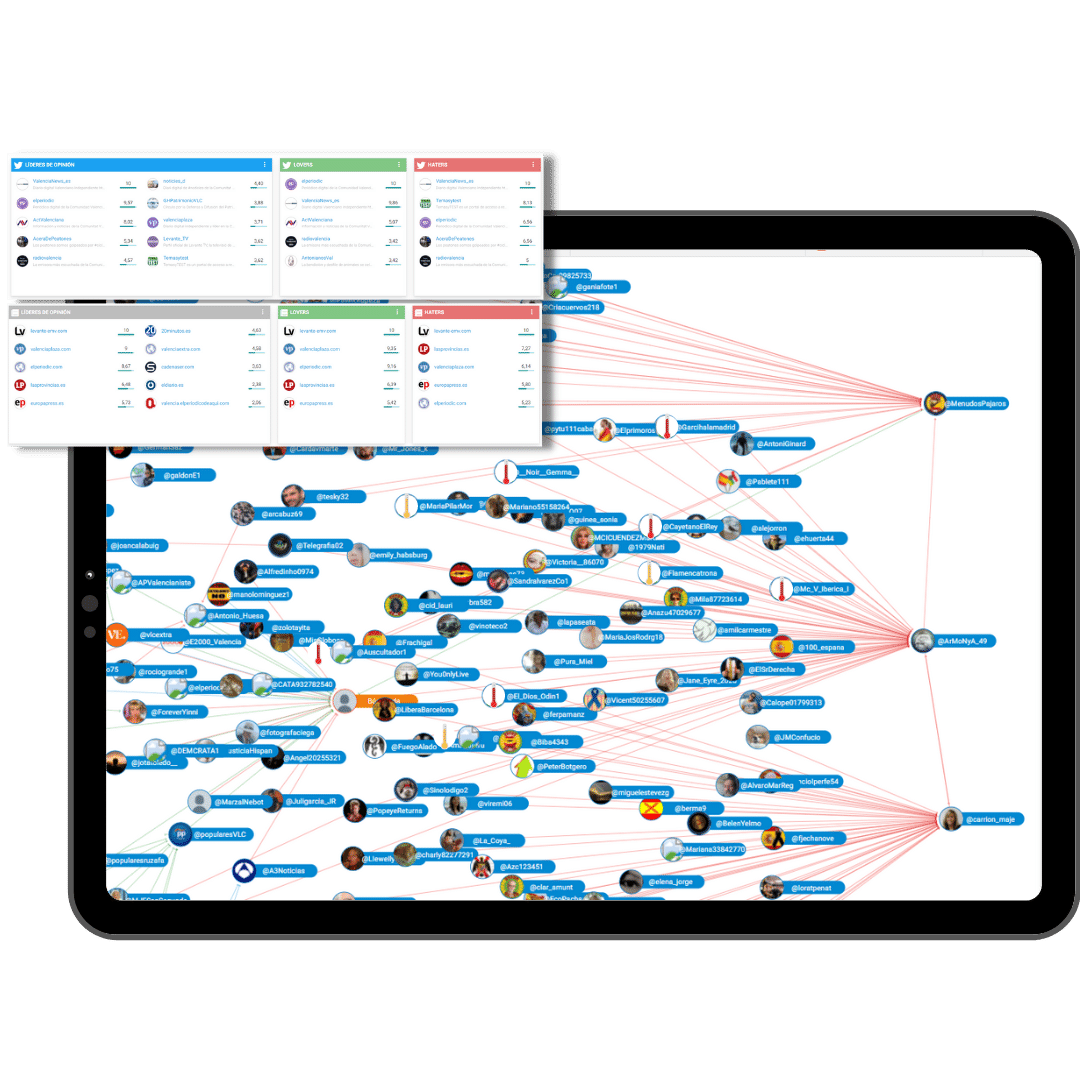
Identificación y análisis de altavoces políticos
DETECCIÓN DE LOS GENERADORES DE CONTENIDO QUE GIRAN ALREDEDOR DE TU MARCA POLÍTICA
Benchmark político
COMPARACIÓN A TIEMPO REAL FRENTE A OTRAS CANDIDATURAS

Nuevas herramientas tecnológicas para la comunicación, la organización, el análisis y la acción política
Nuestra TECNOLOGÍA
Tecnología aplicada a la política 2.0
Big Data e
Inteligencia Artificial
Extracción y tratamiento de millones de datos de forma automática para convertirlos en información e insights
Machine
Learning
Autoaprendizaje automático para predecir comportamientos futuros
Procesamiento del
lenguaje natural
Análisis de sentimientos y semántica de mensajes politicos para la interpretación de datos
Eliminación
de ruido
Optimización de resultados y depuración de datos automática para no sesgar resultados
Nuestra METODOLOGÍA
Extracción, tratamiento y análisis de opiniones obtenidas en Social Media
De las encuestas tradicionales al análisis de opinión en tiempo real
Nuevas metodologías para un mundo en continuo cambio y conectado a la red
Conexiones directas con nuestro votante ideal
Migrosegmentaciones demográficas, por canales, intereses, percepciones y geolocalización
Decisiones basadas
en
datos masivos
Big Data e Inteligencia artificial para automatizar millones de datos
Nuestras fuentes de información
Áreas de aplicación
– Comunicación política
– Asesoría política
– Dirección estratégica
– Estrategia digital
– Campaña electoral
– Marketing
– Gabinete de prensa
– Lobbies
– Políticas públicas
Roles profesionales
– Responsable de Campaña
– Jefe de Gabinete
– Asesor de comunicación
– Digital Strategy
– Community Manager
– Consultor político
– Data Scientist
– Public Affairs Manager
Analiza tu estrategia de comunicación política
Te agendamos una reunión sin compromiso donde te explicaremos cómo Atribus puede ayudarte.
RECOGE CONOCIMIENTO POLÍTICO, TOMA DECIONES ADAPTADAS


